Today I was in the challenge to setup a router. We ware at a meeting with a small wireless router connected to the internet and a couple of hardware with copper interfaces only. We didn't had physical access to the wireless router. We just saw the ESSID to connect to. Luckily I had my notebook running Slackware with a wireless and a copper NIC. The situation was like:
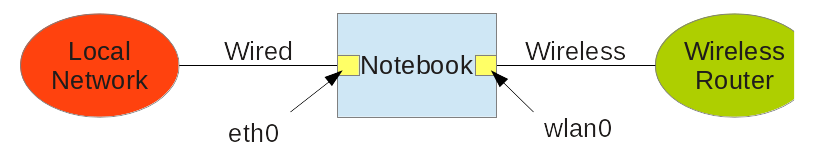
The first thing you need to check is that IP forwarding is acitve. I did that by checking the kernel value net.ipv4.ip_forward with sysctl:
# sysctl net.ipv4.ip_forward
net.ipv4.ip_forward = 0
The above 0 in the output indicates that IP forwarding is disabled. To enable it set net.ipv4.ip_forward to 1 and check again:
# sysctl net.ipv4.ip_forward=1
net.ipv4.ip_forward = 1
# sysctl net.ipv4.ip_forward
net.ipv4.ip_forward = 1
With IP forwarding enabled you need to set a few iptables rules where wlan0 is my external interface an eth0 is my internal interface:
# iptables -t nat -A POSTROUTING -o wlan0 -j MASQUERADE
# iptables -A FORWARD -i wlan0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT
# iptables -A FORWARD -i eth0 -o wlan0 -j ACCEPT
After that any hardware connected to the internal interface eth0 must set the notebooks IP as default gateway eg.:
# route del default
# route add default gw 192.168.1.21
Where 192.168.1.21 is the IP of my notebook. After that all internal clients had access to the wireless router, could setup DNS (resolv.conf) etc.
No comments:
Post a Comment